3. July 2023 By Stefan van der Steen
PGP: What keys are used
In the previous blog I talked about the main features of PGP. In this blog I will talk about the keys that are used.
PGP uses a public and private key combination. Unlike what you might think, you don’t actually have two keys. You have two sets of keys. Both sets contain a parent key and one or more subkeys.
GPG, a well-known implementation of PGP, generates a set of two keys by default. One subkey for signing and compression and one subkey for encryption. This is done because this makes it easy to replace the key for encryption while still using the same key for signing.
Both public and private keys are placed inside a key ring. One for public and one for private keys. All keys can be listed. GPG also marks the (sub)keys to tell which key is used for (S)igning, (C)ompression and (E)ncryption.
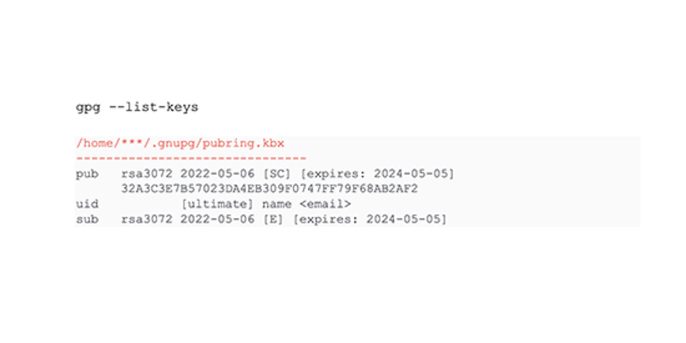
All keys have a unique key id. In the example above this is 32A3C3E7B57023DA4EB309F0747FF79F68AB2AF2. This id is always provided in any message that is signed, compressed and/or encrypted. This way you know which key must be retrieved from the key ring to verify, decompress and/or decrypted.
When creating your own implementation, you should always use the key id to retrieve the key instead of retrieving the first key. This will work with RSA (default), but if you use a DSA/Elgemal combination you will get errors. DSA can only be used for signing and compression.
Tip: when testing your code, add a test which uses a DSA/Elgemal combination. This way you get the error fast. Also, verify the key id to see if the correct one is used.
The default choice in GPG is an RSA/RSA combination with a key size of 3072. It’s possible to choose a different combination. Each key has its own pros and cons. Know that RSA/RSA is usually a safe choice.
One thing to mention is that for RSA a keysize of 3072 is basically the max. You can go higher, but the gains do not outweigh the cons. This is due to the fact that RSA uses prime numbers and the higher you go the least likely you are to come across a prime number. Making RSA become significantly slower, but not equally more secure. If more security is needed it's advised to switch to an elliptical curve cryptography instead of RSA.
Knowing that you actually create a set of keys instead of just two keys helps you to get the long way with your journey with PGP. Remember to always use the key id to retrieve the key from the key ring. This will prevent a lot of unforeseen errors. In my next and final blog, I will talk about the difference between specification and implementation.

